Before proceeding further we recommend that you run a full system scan. In the case of Ploutus, the malware has been on the scene since If the attackertypes this into a machine with Ploutus loaded, he or she is presented with thefollowing:. I agree to my personal data being stored and used to receive the newsletter. Removal You may have arrived at this page either because you have been alerted by your Symantec product about this risk, or you are concerned that your computer has been affected by this risk. 
| Uploader: | Doukinos |
| Date Added: | 14 December 2016 |
| File Size: | 19.17 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 71606 |
| Price: | Free* [*Free Regsitration Required] |
Backdoor.Ploutus
Thatbeing said, it's still very much a real threat, and should not be takenlightly. The NCR memo does not mention the type of jackpotting malware used pliutus U. I'll be using these files for theremainder of this blog post: Delete registry subkeys and entries created by the risk and return all modified registry entries to their previous values. Click lpoutus for a more detailed description of Rapid Release and Daily Certified virus definitions.
Having a Fiesta With Ploutus | Trustwave | SpiderLabs | Trustwave
D malware in a series of coordinated attacks over the past 10 days, and that there is evidence that further attacks are being planned across the country. Thelarge buttons and the drop-down menus make it appear as though this malware mayhave been designed for a touch ploutua, however, we don't know that for sure.
Examples of targeted malware like Ploutus serve as a reminder of the importance of a thorough security review of ATMs and the back-end systems connected to them. If you require its use, ensure that the device's visibility is set to "Hidden" so that it cannot be scanned by other Bluetooth devices. Bills Codigo De Activacion: The following resources may help in identifying suspicious files for submission to Symantec.
ATM jackpotting is hardly a novel, but attacks in the U. Dispense all money in the ATM Activate the Trojan on demand Read all cardholder information entered through the keypad Recommendations Symantec Security Response encourages all users and administrators to adhere to the following basic security "best practices": Subscribe to our newsletter, Threatpost Today!
Upon execution,the malware will hook the keyboard and attempt to look for certain keycombinations. I suspect the reason ATM malware is rare is because it'sdifficult to install because an attacker typically requires physical access to the machine to do so as we sawin this situation where the attackers gained access to the ATM's CD-ROM drives.
Krebs on Security In-depth security news and investigation. Join me on Facebook. For further information on the terms used in this document, please refer to the Security Response glossary.

This should be treated as a call to action to take appropriate steps to protect their ATMs against these forms of attack and lloutus any consequences. These services are avenues of attack. This activation code is generated based on the month and day along witha randomized 4-digit value.

Sep 26, Digital Canaries in a Coal Mine: By default, you should deny all incoming connections and only allow services you explicitly want to offer to the outside world. I agree to accept information and occasional commercial offers from Threatpost partners.
Ploutus.D Malware Variant Used in U.S.-based ATM Jackpotting Attacks | Threatpost
January 29, 5: Specifically, if the following key combination is input into thevictim device, something amazing happens: This is why physical security measures are just as important as cyber. You may have arrived at this page either because you have been alerted by ;loutus Symantec product about this risk, or you are concerned that your computer has been affected by this risk.
By default, many operating systems install auxiliary services that are not critical. Isolate compromised computers quickly to prevent threats from spreading further. The attack group shows a moderate level of sophistication, but the stage is set for MuddyWater to take things to the next level.
I recently acquired two copies of the Ploutus malware. But all that changed this week after the U.
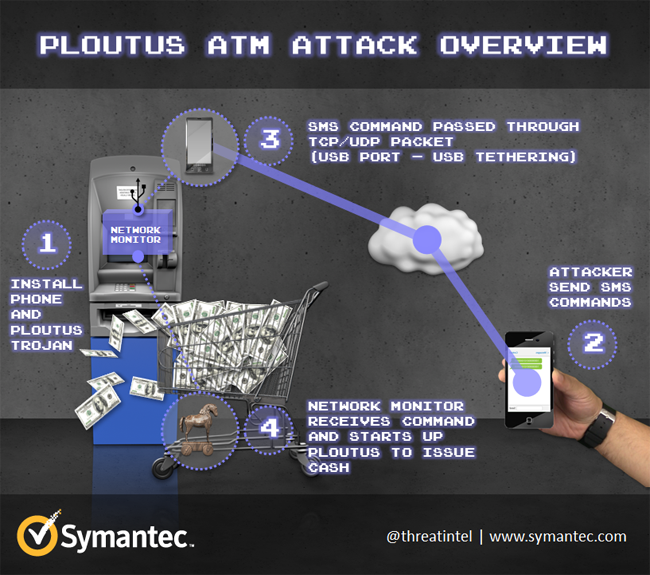
It's always nice when the bad guys give us a GUI.

Комментариев нет:
Отправить комментарий